Welcome to the award-winning BU Research Blog!
Our research shapes and changes the world around us, providing solutions to real-world problems and informing the education we deliver.
Click here to view the full blog, or browse the categories below and with the menu above.
BU staff can login below:
Don’t miss a post!
Subscribe for the BU Research Digest, delivered freshly every day.
BU research
 BU attendance at third annual GCPHR meeting in JuneToday the University of Huddersfield reported online on the international array of over 70 delegates who attended the Annual Meeting... Read more »
BU attendance at third annual GCPHR meeting in JuneToday the University of Huddersfield reported online on the international array of over 70 delegates who attended the Annual Meeting... Read more » Interactive Tangible and Intangible Heritage Applications – BU student work featured in new book chapterAt the beginning of July, the chapter Interactive Tangible and Intangible Heritage Applications Built on Real-Time Graphics Systems: Heritage Experiences... Read more »
Interactive Tangible and Intangible Heritage Applications – BU student work featured in new book chapterAt the beginning of July, the chapter Interactive Tangible and Intangible Heritage Applications Built on Real-Time Graphics Systems: Heritage Experiences... Read more » Second NIHR MIHERC meeting in Bournemouth this weekToday was the first day of strategic planning for the MIHERC project. Our collaborators from Sheffield and Doncaster came down... Read more »
Second NIHR MIHERC meeting in Bournemouth this weekToday was the first day of strategic planning for the MIHERC project. Our collaborators from Sheffield and Doncaster came down... Read more » Second paper for CMWH MRes studentCongratulations to Maryam Malekian, a MRes student in CMWH, who has just published her second paper as part of her... Read more »
Second paper for CMWH MRes studentCongratulations to Maryam Malekian, a MRes student in CMWH, who has just published her second paper as part of her... Read more » AI and Academic Identities: Navigating the FutureThe RKEDF is excited to announce this ECRN seed funded event: AI and Academic Identities: Navigating the Future 📅 Thursday,... Read more »
AI and Academic Identities: Navigating the FutureThe RKEDF is excited to announce this ECRN seed funded event: AI and Academic Identities: Navigating the Future 📅 Thursday,... Read more » PramaLife to present at the at Community Voices Webinar Wednesday 9 July, 12-1pmWe’re excited to welcome Sue Warr, Manager at PramaLife, to our July Community Voices Webinar. Sue will be sharing insights... Read more »
PramaLife to present at the at Community Voices Webinar Wednesday 9 July, 12-1pmWe’re excited to welcome Sue Warr, Manager at PramaLife, to our July Community Voices Webinar. Sue will be sharing insights... Read more »
international
PG research
Research lifecycle
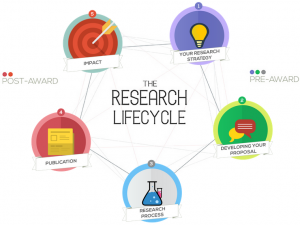 Our Research Lifecycle diagram is a jazzy interactive part of the BU Research Blog that shows the support and initiatives that are available to staff and students at each stage of the research lifecycle.
Our Research Lifecycle diagram is a jazzy interactive part of the BU Research Blog that shows the support and initiatives that are available to staff and students at each stage of the research lifecycle.











